Keycloak as a Service: Integrated Support for SPID and CIE Authentication
Keycloak in SaaS mode is a solution designed for authentication via SPID (Public Digital Identity System) and CIE (Electronic Identity Card). This platform offers a powerful tool for managing digital identities, ensuring compliance with the standards required by Public Administrations.
SPID Authentication Solution with Keycloak
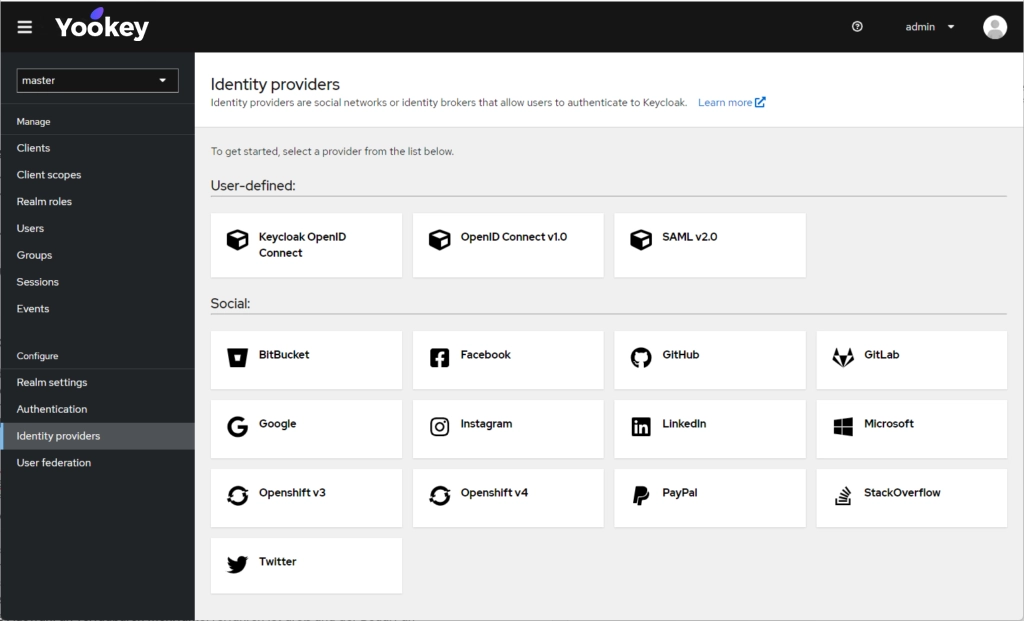
The integration allows Keycloak to be used as an Identity Provider (IdP) for managing authentication through SPID. SPID uses the SAML 2.0 protocol, and to integrate it correctly, Keycloak must be configured according to the official SPID specifications and guidelines. The configuration process consists of two main phases:
a) Initial Configuration Phase
To configure Keycloak as the Identity Provider for SPID, you need to access the Keycloak administration panel. Once logged in, select the realm where you want to enable SPID and navigate to the “Identity Providers” section. In this section, choose the SAML v2.0 option to integrate SPID as the Identity Provider.
Next, some key parameters must be configured, such as the URL of the Single Sign-On Service, provided by the SPID Identity Provider. Once this configuration is complete, the next step is to manage the metadata. The metadata provided by SPID must be downloaded and uploaded directly into the Keycloak configuration panel to complete the process.
b) Integration Testing Phase
After the configuration is completed, it is essential to test the integration with SPID to ensure everything is functioning correctly. You can use a test environment to verify that the integration meets the required standards.
CIE Authentication via Keycloak
The Electronic Identity Card (CIE) uses the OpenID Connect (OIDC) protocol and requires a configuration based on this standard. The configuration involves the following key steps:
- Create an OIDC Client
To configure a client in Keycloak, go to the “Clients” section in your realm and create a new client. Assign a Client ID that will identify the application and select OpenID. - Configure the CIE Parameters
Once the client is created, configure the specific parameters required for integration with CIE. This includes setting the authentication endpoints and managing the configuration information. - Define the Authentication Scheme
Configure the authentication scheme in Keycloak to ensure proper communication with the CIE authentication system. - Manage User Attributes
Manage and map user attributes from the CIE, such as first name, last name, tax code, and other data, so that they can be correctly used within Keycloak for authentication and access management.
Benefits of Keycloak in SaaS with SPID and CIE
Among the main benefits of using Keycloak with SPID and CIE, the following can be highlighted:
- Multi-tenant: A single system can manage multiple organizations or clients, each with its own SPID and CIE configurations.
- Security: SPID and CIE ensure high standards of personal data protection.
- Regulatory Compliance: Suitable for companies or organizations.
- Customization: Supports flexible integration and SaaS applications.
- Ease of Use: User-friendly interface for managing users and configurations.
Yookey ID
Yookey ID is an advanced solution based on Keycloak in SaaS mode, designed to serve as an access point for SPID and CIE. This platform seamlessly integrates authentication systems, providing an effective response to the needs of Public Administrations and private enterprises.
Thanks to Yookey ID, it is possible to ensure secure access that is fully compliant with Italian regulations, simplifying user authentication processes and significantly improving their access experience.
Ready-Made Templates
Would you like more information?Contact our sales team to discover the available solutions.