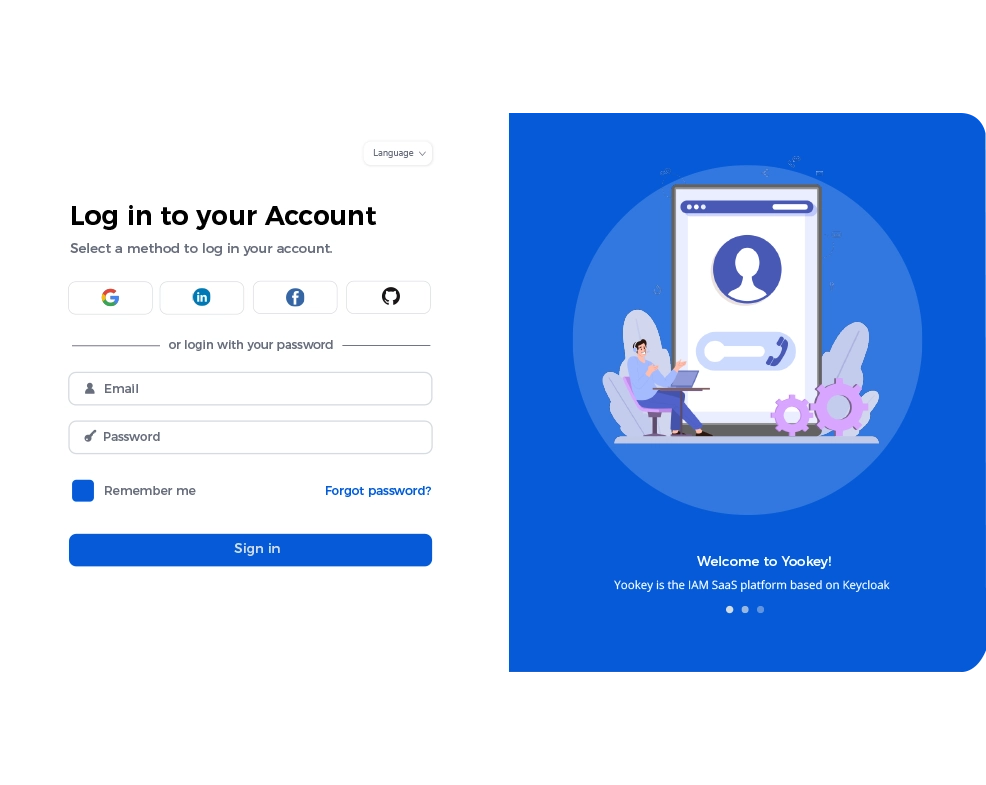
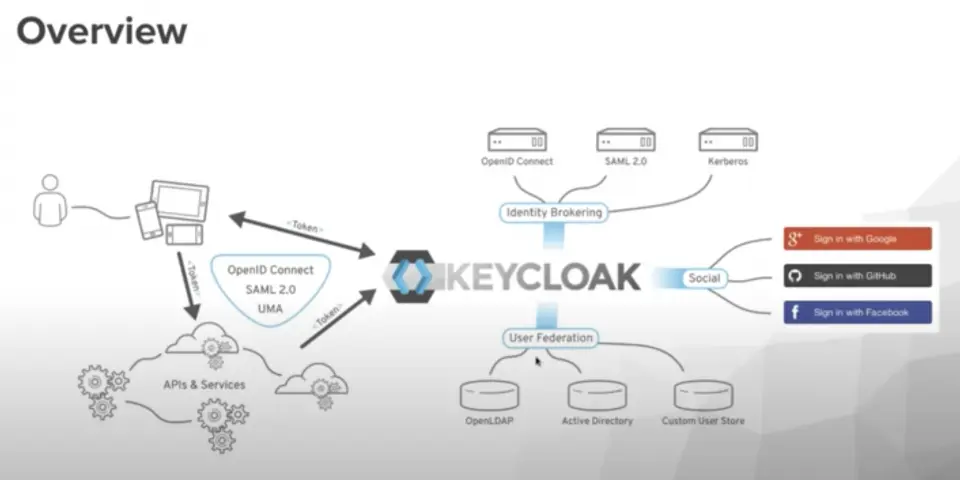
IAM and Identity Lifecycle: security from Onboarding to Offboarding
What is identity lifecycle management (ILM)?
Identity lifecycle management (also known as user lifecycle management – ULM) is an approach that enables organizations to manage users’ digital identities and access rights in a secure, efficient, and consistent manner.
This framework covers the entire user lifecycle, including identity creation and onboarding of new employees, potential privilege updates due to role changes, and the revocation of access during the offboarding phase.
IAM: why it’s essential for enterprise security
An Identity and Access Management (IAM) system ensures that only authorized users can access critical business resources. By implementing controls such as the principle of least privilege (PoLP), multi-factor authentication (MFA), and single sign-on (SSO), IAM plays a crucial role in reducing the risk of unauthorized access.
Additionally, IAM systems support regulatory compliance by generating detailed logs and audit reports, while continuously monitoring for suspicious activities and anomalies.
Automating tasks related to account creation, modification, and deactivation minimizes human error, improves operational efficiency, and allows for faster responses to critical events.
Ready-Made Templates
Are you looking for an IAM system?Visit Yookey’s website to explore the available solutions.
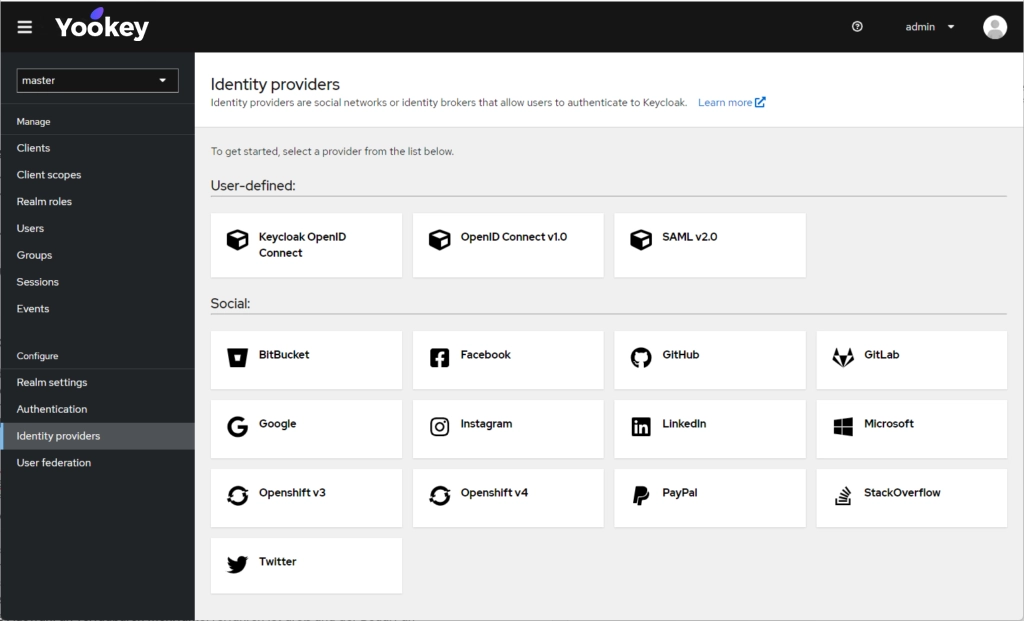
Digital Onboarding: how to assign access securely and automatically
Digital onboarding is the process of integrating new employees or customers using digital tools and solutions. To ensure timely, secure, and automated access assignment during this phase, IAM systems must be integrated with user lifecycle management (ULM) solutions.
Automating the provisioning of accounts and associated privileges ensures that new users have immediate access to the necessary company resources. This approach speeds up integration, reduces risks tied to misconfigurations or delays, and optimizes the use of IT resources.
The security of digital onboarding is reinforced by applying key principles such as the principle of least privilege (PoLP), which ensures users are granted only the access necessary for their tasks, thereby mitigating the risk of insider threats.
Supporting these principles are advanced technologies such as:
- Single sign-on (SSO), which simplifies the user experience by allowing access to multiple applications with a single set of credentials.
- Multi-factor authentication (MFA), which adds additional identity verification layers to secure access.
Secure Offboarding: how to revoke access and prevent insider threats
Secure offboarding protects company assets by ensuring that all access rights are promptly and completely revoked and that the digital identity of a former employee is deactivated at the end of their employment.
To mitigate these risks and prevent data breaches, it is essential to adopt an automated approach to deprovisioning. By automating the revocation of access rights, organizations can ensure that authorizations are removed quickly and accurately, improving operational efficiency and significantly reducing human error and unintended exposure.
Yookey, the Identity & Access Management software
Yookey ensures secure and efficient onboarding and offboarding processes through integration with single sign-on (SSO) and the automation of access management.
During onboarding, users automatically receive the appropriate permissions based on their role, with the addition of multi-factor authentication (MFA) to ensure a high level of security from the very first access.
At the end of the employment relationship, offboarding is handled in a centralized and immediate manner: all access rights are revoked simultaneously across all connected applications, eliminating the risk of orphaned accounts or residual privileges.
The entire lifecycle is fully tracked and documented, ensuring compliance with regulations such as NIS2 and ISO 27001.
Speak with our sales team to learn more